Full Guide - How to Use Aimon for Mac
A step-by-step guide on how to monitor Mac computer with Aimon for Mac
Steps for usage
Step 1: Create an Aispyer account.
Step 2: Install and activate Aimon for Mac on a Mac computer.
Step 3: Login to your account and view all tracked data.
Step 2: Install and activate Aimon for Mac on a Mac computer.
Step 3: Login to your account and view all tracked data.
If you want to learn more about Mac computer monitoring with Aimon for Mac, please follow the detailed step-by-step guide below.
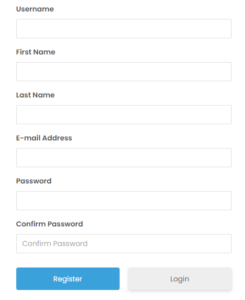
Create an Aispyer account
Click on Register button to create an Aispyer account with your valid email address and password. After that, you have to select a plan of Aimon for Mac in order to use all advanced monitoring features of it. There are two plans on the pricing page of Aimon for Mac. You can choose one that suits you.
Install and activate Aimon for Mac on a Mac computer
After purchase, an email will be sent to your registered email automatically. Using the download link, download and install Aimon for Mac on the target Mac computer. After installation, you can continue to activate it by entering your License Key and click the ACTIVATE button.
Note:
If you have problem in installing and activating it, please login to the dashboard with your account, click help in the upper left corner, find "Reference Manuals", then select "Installation & Activation". You will see the detailed installation and activation guide.
Login to your account and view all tracked data
After activating the app, login to the online dashboard with your User Id and Password, then you can use all advanced monitoring features of it.
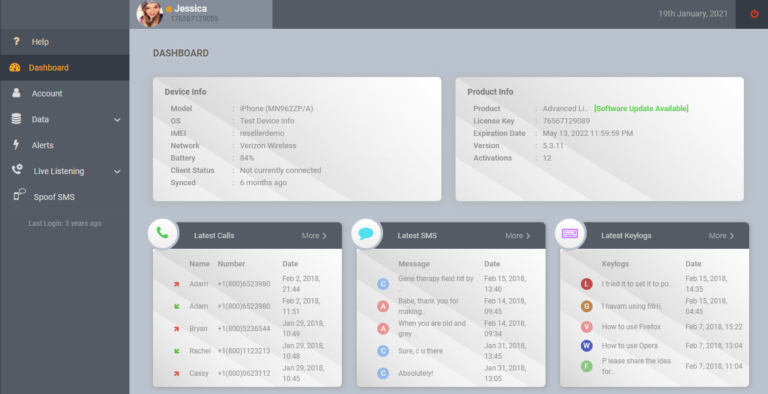
What can Aimon for Mac help you?
1. Monitor IMs:
View the contents of the most popular IM chats – Facebook, LINE, WhatsApp, etc. – even those that have been deleted
2. Verify Network Activity:
Keep track of all computer network connections – including bandwidth usage, user logins and even print jobs – that take place.
3. Spy on Internet Activity:
View browsing history and bookmarks, including URLS, date and time of visit, giving full visibility of browsing history.
4. Keylogger:
Our keylogger lets you see everything that’s typed – even if it’s deleted. Discover search terms, notes and more.
5. Read Emails:
Instantly read all incoming and outgoing emails, as well as the time-stamp and contact details of the sender.
6. Safeguard Your Data:
Know when a file was opened, who modified it and where it was sent with our file transfer and activity tracking feature.
View the contents of the most popular IM chats – Facebook, LINE, WhatsApp, etc. – even those that have been deleted
2. Verify Network Activity:
Keep track of all computer network connections – including bandwidth usage, user logins and even print jobs – that take place.
3. Spy on Internet Activity:
View browsing history and bookmarks, including URLS, date and time of visit, giving full visibility of browsing history.
4. Keylogger:
Our keylogger lets you see everything that’s typed – even if it’s deleted. Discover search terms, notes and more.
5. Read Emails:
Instantly read all incoming and outgoing emails, as well as the time-stamp and contact details of the sender.
6. Safeguard Your Data:
Know when a file was opened, who modified it and where it was sent with our file transfer and activity tracking feature.